Security Seals 101: From the Cyllinder-Seals made of clay To Security Seals with Traceability
1.1 -Definitions. Seals x Keyed-Padlock. Security Systems Efficiency in Sealing
Security Seal is a device intended to leave evidence of tampering, not unambiguous. Unlike the padlock, the seals are not necessarily meant to delay or resist unauthorized access, but merely record that it has taken place.
Padlock: device that delays unauthorized entry or removal of the items it aims to save. Any padlock may be opened by a sufficiently motivated person. Seals x Padlock: A seal does not necessarily have to withstand an opening.
In other words, sealing is not padlock.
Several seals are made of plastic and can be opened or destroyed.
"They can be opened" means that the fraudster should create special tools for the violation, eventually have access to well-kept patents and even set up a complex industrial system for the making of the same seals as those that will be violated. The Mint manufactures paper money with special characteristics to prevent counterfeiting, but nevertheless seeks to modify the process from time to time to complicate the investigations and inventions of the fraudsters.
Some devices, designated as Barrier Seals and Semi-Barrier Seals, even offer a "barrier" or physical resistance, in order to delay its opening.
The effectiveness of the seals strongly depends on the security system adopted for their acquisition, storage, registration, application, inspection and removal. With a good security system, a modest seal can provide excellent security, while a sophisticated seal used improperly can totally fail the purposes for which it was proposed.
1.2 – History
1.2 – History:
Archaeologists working in the area where the earliest civilization flourished, the Sumerian (VI millennium before the Christian era), report that in all excavations there were always remains of cylindrical stone or metallic seals with which they were prepared, in clay, intended for storage of cereals and other products.
We can consider them as the first security seals manufactured in the world, since they guaranteed exclusivity to the operations carried out - the artistic complexity of the sculpted figures was not something that could be reproduced.
The antiquity of the use of the seals is attested by quotations from the Bible (Song of Songs, the seven seals that keep the secret of the Apocalypse, etc.).
Its use with wax impressions is common in everyday life from the fourth millennium BC.
But its greater diffusion within all the social groups only took place from the centuries 12-13 of our era.
In the Middle Ages, in the occasion of the death of the owner of a seal, it was used to bury the matrix with the deceased or to destroy it (even today, the Pope's ring is buried with him, before being destroyed the lead seal contained therein).
1.3 – Evolution
1.3 – Evolution
First Generation: From the beginning of civilization to the Industrial Revolution, we have a First Generation of Security Seals, in clay, wax, gold or silver, where artisans engrave seals and rings in high relief, guaranteeing exclusivity to the sealing operation. The seals were present in the greatests moments of history, as in the example presented here of the letter of the English nobles in 1530 to Pope Clement VII: the Pope's refusal to comply with the request for annulment of the marriage of King Henry VIII marked the break with Rome Of the English church, that happened to be led by the monarch.

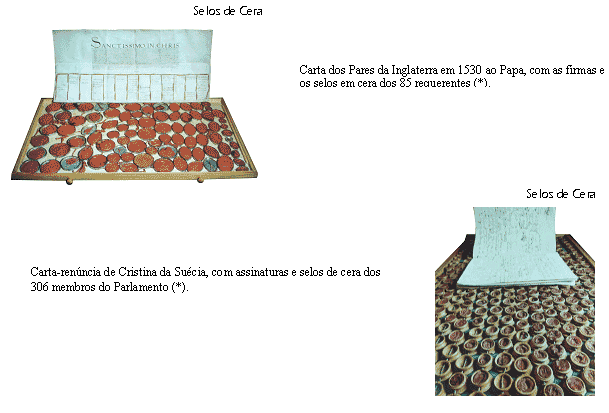
A maximum of exclusivity was introduced with the Golden Seals, initiated in the Byzantine Empire and later used in Europe by high dignitaries such as kings and popes.
(*) Photo of the book "I Sigilli d'Oro dell' Segreto Segreto Vaticano", edition Franco M. Ricci
What we call the First Generation of Security Seals had met and satisfied the needs of the world back then. In the last two centuries, however, the Industrial Revolution and, more recently, increasing globalization and the population growth, have led to the increasingly rapid evolution of security seals.
Indeed, the evolution of the seals is a consequence of technological developments, the advent of new materials, the demands for ever greater levels of security, the evolution, finally, of fraudsters - always discovering new methods of violation, New production methods, etc.
Second Generation: Metal seals applied by pliers.
With the Industrial Revolution the manufactured seals emerge, gaining prominence the ones made of lead material. The exclusivity was given by marking pliers and unique dies - each user was identified by their own die.
Lead sealing tends to disappear completely because of its carcinogenic potential and contamination of the soil, besides being easily infringed and banned in many countries.

Third Generation: Seals numbered by primary processes of hot stamping.
The passage to the mass production of security seals and the need to control the applications have made it unfeasible to use sealing pliers.
At the same time, the advent of computers made it possible to adopt number as an element of differentiation from one sealing to another.
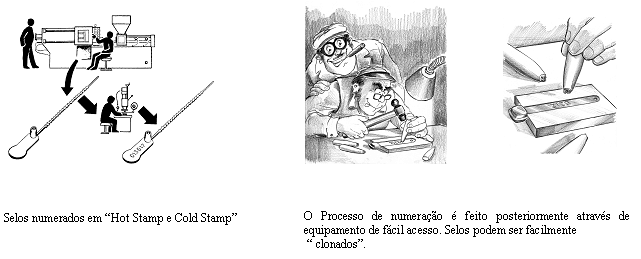
Fourth Generation: Seals with numbering molded in high relief.
In 1990, ELC, which was the first company in the world to commercialize (back in 1967) a polypropylene security seal, patented in Brazil and then in the US, its industrial process of embossed numbering on the sealing tab, injected-molded at the same time as the seals themselves.
This evolution was of great importance for the security sealing world. The "cloning" or duplication of the seal is now impossible, because it will not be possible to duplicate a high-relief numbered seal. Each embossed numbering seal is as unique as a human-fingerprint.
.

In fact, the best that a fraudster could do, as a "response" to the high-relief numbered seal, would be to try to make the so-called "false embossing" obtained by punching the back of the blade. For example, the cards credit numbers are pressed on one side and raised on the other.
Fifth Generation: Smart numbered seals with barcode and check-digit.
There is an important factor to consider called human error. Conscious or not, this chance of error with seals is eliminated when numbers/barcodes are scanned into the system instead of transcribed by humans.
ELC uses unique process to apply barcode numbers to the seals, such as "in mold labeling" (IML), in which a film or paper with bar code and check digit is fused to the seal during the injection-molding process.
Laser Mark – State-of-the-art laser marking equipment apply indelible barcode numbers on the seal’s tab and/or capsules.

1.4 - Sixth Generation: Traceability – Item 1.4.1
1.4 - Sixth Generation: Traceability
1.4.1 - Sixth Generation TIDs (Tamper Indicative Devices).
The control and traceability of the various stages of modern economic life has become a necessity with which humanity coexists daily, such as:
• Control of the origin and quality of the food we consume;
• Control of access of people, animals and objects to restricted areas or countries;
• Control of services that provide electricity, water, gas and fuel;
• Control of amounts, cash, checks, credit cards, telephones, transportation, weights and measures.
The need for sealing and its control, which had previously been of interest to only a few individuals, is now of national and even global interest. ELC, analyzing this market need, concluded that there was a lack efficient control of the traceability of TIDs - Rape Identification Devices, the modern designation that encompasses seals, envelopes and security pouches. As a solution, ELC developed and registered a more efficient traceability control in the of the TID’s be it a seal (see our Evolution of Sealing), be it a pouch or a Security envelope. As a solution, ELC developed and registered copyright on web-based software called “ELO DE SEGURANÇA®” or “VIRTUAL SEAL”. It is a system to trace the entire trajectory of a TID, based on its numbering / coding, applicable in all companies that need to discipline their sealing procedures of different objects.
The tracking of the TIDs was thoroughly studied by the US Department of Defense (DoD) and the Department of Homeland Security (DHS) together with the Los Alamos National Laboratory through its Vulnerability Assessment Team (VAT) team, which reached some important conclusions :
1 - "In order to recognize the security of a seal, it must obey rules or procedures regarding the acquisition, storage, distribution, application, registration, inspection, training and disposal of seals, the so-called" SEALING PROTOCOL "( "Security Seals Protocol"). Failure to comply with the standards for any of these steps will compromise the safety level of the seals selected. "
2 - "Seals are part of a safety program / procedure and should not be considered in themselves the only line of defense". As part of his work, the Los Alamos team analyzed 213 different detail seals, some from the US Government and others from private manufacturing. These seals had prices and features that ranged from low cost and technology to high cost, reusable, and high technology seals like active RFID seals. Among other results, it was verified that, by adding US $ 1.00 to the cost of a more elaborate seal, the time needed for its violation only increased by 2 seconds. The average unit cost of a potential violation would increase by US $ 0.27 when we add the unit cost of US $ 1.00 per seal. That is, the high-tech features are only a distraction or an onerous failure to observe some critical items of vulnerability of the sealing system. Therefore, it is more important and economical to incorporate the implicit costs in the "Sealing Protocol" than to record unit costs with the most elaborate sealing technology.
Annex A, issued by the International Organization for Standardization, complements the work of DoD and DHS by noting in Annex A that in the various stages of the life of a TID, from its acquisition to its removal and disposal, there are Security breaches. Although the Norm referred to was conceived for container sealing, the principles therein also apply to DIVs used in other seals. In summary, the "Sealing Protocol" involves:
QUALIFICATION OF THE SUPPLIER
Acquisition of DIVs
. Verify that the supplier has ISO 9001: 2012Certification;
. Whether the literature and specifications of its products are based on international standards;
. If the supplier is not outsourcing its production and, if this is the case, seek to locate the source of production of its original parts or finished products for future traceability;
. Limit acquisition to few manufacturers;
. Identify the models of DIVs and their characteristics for use and training;
. Adopt technical specifications based on sealing industry standards;
. Maintain records of acquisitions;
. Limit the incidence of DIVs acquired with duplicate numbering / coding to 0.1%.
Storage of DIVs
. Store the products safely and strictly control, which implies limiting access to the Warehouse and data on the numbering of DIVs.
Control and Distribution
. In the Warehouse, the DIVs will be registered according to their serial number;
. Establish a "chain of responsibility": inventories will be verified at each turn of the shift.
Application of DIVs
. Before the application, examine the DIVs for defects and discoloration, comparing their numbering characteristics, format, measurements, etc. With those of a DIV model;
. The locking of the DIV depends on its correct application, and its sealing behavior must be checked to avoid a false closing;
. The closure of the DIV shall follow the rules recommended by the manufacturer for each model;
. Sealing without observing the details listed above will make the installer of the DIV responsible for potential fraud, as it will characterize a "pre-violation".
Numbering / encoding registration
. The numbering and other identification data of the DIVs will be recorded and tracked either manually or by bar code or RFID, in order to guarantee the connection link with the serial number of the closed object.
Inspection of DIVs
. The DIVs will be thoroughly inspected to verify the occurrence of possible fraud;
. It is worth mentioning that it is necessary the detailed knowledge of each DIV, its fragilities and suspicious points to be checked.
Removal of DIVs - Interpretation of verified data
. For a reliable inspection, the removal of the DIVs will be done according to a previously approved method, in order to guarantee conditions for the correct interpretation of the collected data;
. The DIV should be treated as evidence of violation, should it occur. Therefore, it is necessary to strictly guard it, together with the object inspected, so that both will be tried by independent laboratory.
Discarding the DIVs
. DIVs cannot go to the common trash, because they contain data useful to fraudsters;
. The agent who does not keep the evidence commits a crime of "file burning";
. The used DIVs and their parts will be collected for proper analysis and destruction.
Training
. Use literature created by the manufacturer on the correct use of DIV;
. To pass on these and other knowledge to users, outsourcers, employees and other suppliers of DIVs for effective sealing;
. As an integral part of a training program, it is important to study ISO 17712, particularly its Annex A. Although drafted for container seals, it is applicable to seals in general, including international practices recommended for manufacturers and Users.
1.4 – Sixth Generation: Traceability Control – Item 1.4.2
1.4 – Sixth Generation: Traceability Control
1.4.2 – Manufacturer Traceability Control
Throughout nearly 50 years of experience, ELC has developed specially designed standards to facilitate the control of the application of the seals by its customers, mentioned below.
A) Control in the purchase
Upon receipt of a new order, ELC checks in its system for the last numbering on the seals already supplied to the customer, in order to eliminate the possibility that seals with the same numbering as a previous order will be produced.
Afterwards, all the characteristics of the new order are sent to the system: model, numbering, color, quantity, deadlines and prices.
B) Control in manufacturing
At the start of the production of an order for safety seals, ELC will carry out regular inspections of the injection machines in order to control the quality of the seals manufactured.
At the end of each production shift, the total manufactured is recorded, giving rise to quantity control.
Once the seals are produced, the final inspection is carried out in accordance with the NBR Standard (ABNT - Brazilian Association of Technical Standards).
A sample is then collected to be submitted to 3 tests:
• visual - to ensure the colors produced and whether the seals have marks or stains that compromise their aesthetics.
• functional - when testing whether the seals are closing tightly, if excessive hardness of material occurs, etc.
• of violability - when it is verified, once the seal is closed, if it is possible to open it without leaving a mark of violation.
The last control in the factory is the so-called "final closing", when all the data contained in the order are compared with the production ready and finished.
C) Control of distribution
The customer will receive the seals in bags usually with 100 units, each of which will receive a key number. With the seals, the customer receives a "software" that will allow him, once the key number of any bag has been entered, to know the number of all 100 seals contained therein. The system allows the control of the distribution in cases of:
• random seals without repetition
• seals with sequential numbering
• seals with coded sequences
It is important to note that, in the invoice issued by the factory, the first and last number of the set of seals is provided.
1.5 - Evolution of Packaging
I – Lacres de Segurança: dos cilindros marcados em argila ao controle por software
1.5 - Evolution of Packaging
The evolution registered in the sector of security seals has had a consequence in the modernization of the security packaging represented by bags, pouches and envelopes, destined to the custody and transport of documents and values. For centuries the best pouches were of the chest-type, padlocked and keyed, as in the illustration on the side.
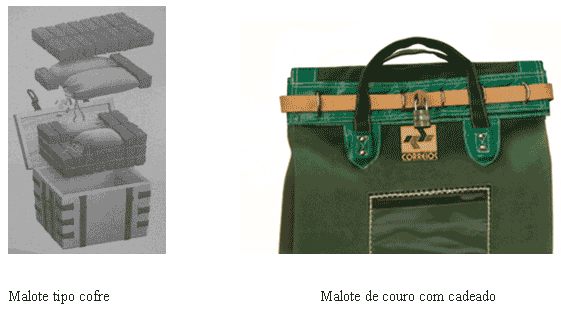
At the time of the diligences and with the acceleration of the commercial relations came the leather bags, closed with a belt, buckle and padlock, a formula that for centuries seemed destined to continue. However, manufacturers of plastic safety seals in the second half of the 20th century realized that the developed seals could have immediate application in the increased security of envelopes and pouches.
This perception came from the level of security that those products were able to attain at that time and that they were not. On one hand, envelopes closed with hot melt and later on with void tape could be opened accidentally in the face of extreme temperatures or also fraudulently with the application of freezing spray.
On the other hand, the pouch - safe and then the leather pouches with padlocks and even the zippered pouches were far from being barred or at least detecting the tampering signs.
1.5 – Evolution of Packaging - Item 1.5.1
1.5 – Evolution of Packaging
1.5.1 – Maximum security envelopes
Then, comes the maximum safety disposable plastic envelope, with solid polypropylene closure, impossible to be tampered without leaving a trace, immune to variations in temperature and freezing spray.


1.5 - Evolution of Packaging - Item 1.5.2
1.5 – Evolution of Packaging
1.5.2 – Evolution of Packaging
Within the concern for the environment, the envelopes and semi-disposable systems appeared, of which the following products are examples.


1.5 - Evolution of Packaging – Item 1.5.3
1.5 - Evolution of Packaging
1.5.3 - Oxy-biodegradable envelopes
The latest development in the manufacture of safety envelopes, which was born out of ecological concerns, was that of the oxy-biodegradable envelope. An unwanted durability, estimated in hundreds of years, of plastic envelopes and sacks, of which the world consumes one million tons per minute, turns these materials into the residue that most pollute cities, fields and oceans. The solution was recently suggested by the English company Symphony, through oxy-biodegradable plastic technology, by which an additive is injected into the plastic while still in the melting state, so that after some time (programmable, ranging from 60 days to 6 Years), the molecular chain of the plastic breaks down, resulting in water and small amounts of carbon dioxide and biomass, not harmful to the environment. It is likely that this new technology will be a turning point in the evolution of plastic consumption. Anyone who is not prepared for the change will have difficulty maintaining their business because they can not meet their customers' needs and environmental claims. There are already reports of heavy fines applied in Brazil to establishments that are not consuming oxy-biodegradable plastic bags here, unlike their counterparts in the same groups in other countries. ELC, in anticipation of this new trend, started to manufacture oxy-biodegradable security envelopes for several customers, having registered a positive reaction above expectations. Properly authorized by the holders of this technology, these ELC products carry the demarcation mark - D2W.
1.5 - Evolution of Packaging – Item 1.5.4
1.5 – Evolution of Packaging
1.5.4 – Security Bags
Safety pouches Regarding pouches, the security closure industry has renewed the market by taking its products to ensure the inviolability of previously known pouches.

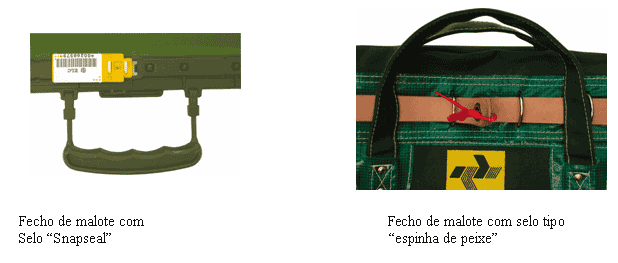
In summary, the security closure industry today produces seals, envelopes and pouches of a completely different style than the products that reigned in the market until the late 1960s. Today, state-of-the-art is composed of seals In high relief and/or "smart" bar code numbers, check digit and software control, along with envelopes and pouches with mechanic closure (non-adhesive). The industry met the growing demands for security but it also evolved to contribute to a better conservation of natural resources and respect for ecological concerns.
